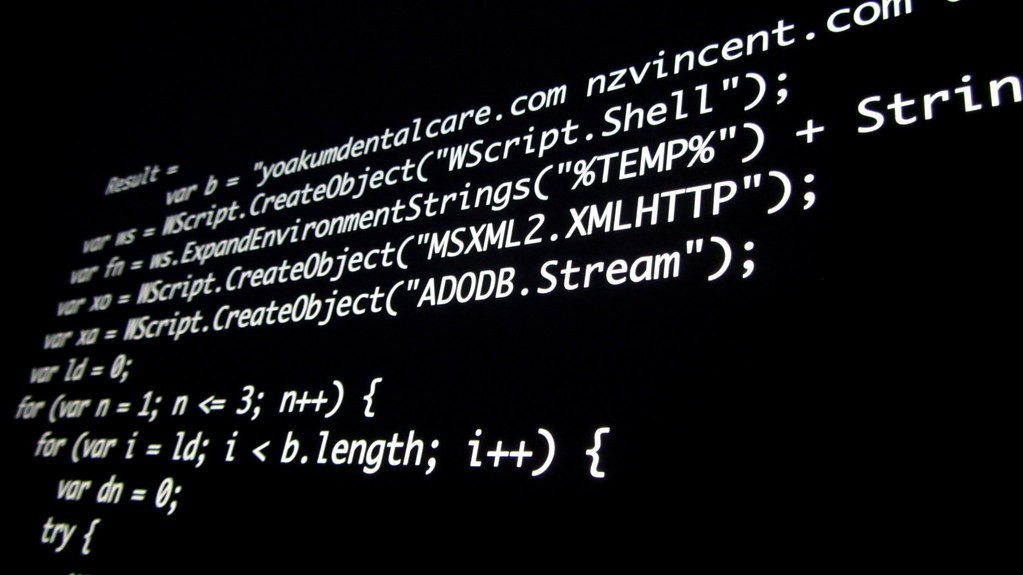
A recently discovered Visual Studio Code extension named “Vibe” has been exposed as a malicious package designed to infiltrate developer systems and compromise software supply chains. Security researchers found that the rogue extension, disguised as a legitimate development tool, executed stealthy code injections capable of harvesting credentials, manipulating repositories, and exfiltrating sensitive project data to remote command-and-control servers. The attack underscores the growing vulnerability of open-source ecosystems and integrated development environments (IDEs) to sophisticated cyber-espionage campaigns. The compromised extension was distributed via unofficial marketplaces, exploiting developer trust to embed itself into daily workflows. Experts warn that similar attacks are increasingly being weaponized by state-linked groups to target critical infrastructure and private-sector developers worldwide.
Sources: Hacker News, Bleeping Computer
Key Takeaways
– The “Vibe” VS Code extension masqueraded as a legitimate tool while secretly stealing developer credentials and project data.
– The attack highlights the risks of using unofficial or unverified marketplace extensions in development environments.
– Cybersecurity experts link such operations to a broader rise in state-sponsored and criminal supply chain attacks targeting critical digital infrastructure.
In-Depth
The discovery of the malicious “Vibe” extension for Visual Studio Code marks yet another escalation in the ongoing war over digital sovereignty and software security. According to multiple cybersecurity research firms, the extension was deceptively packaged to appear useful to developers, while in reality it injected hidden scripts into active development environments. These scripts siphoned data ranging from repository credentials to proprietary code snippets, sending them to remote servers under the attackers’ control.
This tactic preys on the open-source ethos of trust and collaboration. Developers are often encouraged to share tools and enhancements, but that openness has now become a liability when hostile actors exploit it. The “Vibe” case proves that hackers no longer need to breach corporate firewalls directly—they can compromise the creators of the software themselves. That’s a disturbing shift in the cyber battlefield: rather than storming the gates, attackers now poison the well.
From a broader perspective, this development underscores how deeply intertwined national security and digital infrastructure have become. In recent years, state-backed hacking groups from China, Russia, and North Korea have targeted everything from defense contractors to healthcare systems through software supply chains. The line between criminal enterprise and geopolitical warfare is blurring. Every compromised line of code can become a weapon in that fight.
The conservative takeaway is simple: dependency on globalized, unvetted software sources leaves America’s innovation pipeline dangerously exposed. Without stronger code verification, localized development controls, and stricter oversight of open-source contributions, we’re inviting adversaries into the heart of our technological systems. Developers, businesses, and federal agencies alike must wake up to the reality that today’s code repositories are tomorrow’s front lines.