Microsoft has raised the alarm over a new strain of modular malware known as PipeMagic, which is being disguised as a ChatGPT desktop application to sneak into systems via GitHub; exploiting a zero-day elevation-of-privilege vulnerability in Windows Common Log File System (CVE-2025-29824), PipeMagic serves as a stealthy backdoor and infostealer with dynamic payload execution, encrypted inter-process communication, and self-updating capabilities, affecting select victims across IT, financial and real-estate sectors in the US, Europe, South America, and the Middle East.
Sources: DarkReading, Hacker News, TechRadarPro
Key Takeaways
– Modular and Stealthy: PipeMagic delivers payloads in memory, communicates via encrypted named pipes, and supports modules loaded from command-and-control servers.
– Zero-Day Exploit at Play: The malware leverages CVE-2025-29824—a critical Windows CLFS flaw patched by Microsoft in April—but many systems remain vulnerable.
– Geopolitical and Sector Spread: Though seemingly limited in scope for now, victims span multiple continents and sectors including IT, real-estate, finance, and more.
In-Depth Article
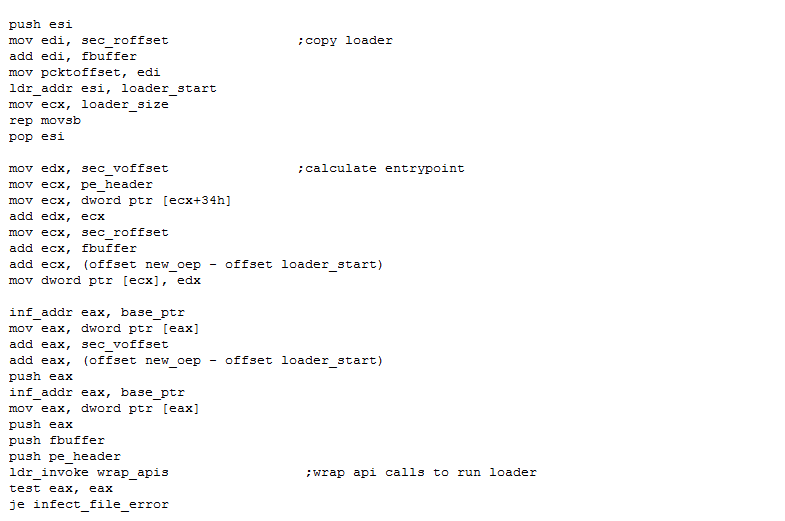
Microsoft is sounding the alarm on PipeMagic, an advanced malware framework camouflaged as a familiar open-source ChatGPT desktop app. Attackers have hijacked a legitimate GitHub project—slipped in malicious code—and packaged it into an in-memory dropper. Once executed, the dropper decrypts and launches the embedded malware directly into system memory, leaving little trace on disk.
What really sets PipeMagic apart is its modular architecture. It can dynamically load payloads via encrypted named pipes, maintain communication with command-and-control servers, escalate its privileges, and even update itself—all without touching a file on disk. The entire operation revolves around exploiting CVE-2025-29824, a critical Windows vulnerability in the Common Log File System that Microsoft patched earlier this year. Unfortunately, unpatched systems remain exposed, and PipeMagic has shown capability in executing ransomware and backdoor infections across IT, finance, and real-estate targets in regions spanning the US, Europe, South America, and the Middle East.
Security firms like Kaspersky and BI.ZONE have confirmed that PipeMagic has resurfaced in “Play” ransomware campaigns, reaffirming its evolving threat. The risk? Even a trusted open-source appearance can be lethal. Organizations should treat every third-party app with suspicion, patch promptly, and ensure their detection tools are configured to catch this kind of in-memory modular malware. Vigilance remains the best defense.