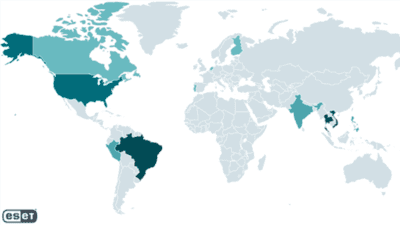
A fresh investigation by Slovak cybersecurity firm ESET uncovered a previously unknown threat group dubbed GhostRedirector, active since at least August 2024, which covertly compromised at least 65 Windows servers across Brazil, Thailand, Vietnam, the U.S., Peru, Canada, Finland, India, the Netherlands, the Philippines, and Singapore. Using two custom tools—Rungan, a stealthy C++ backdoor that executes commands and even creates admin users, and Gamshen, a sneaky IIS module that intercepts Googlebot requests for SEO fraud to promote gambling sites—the group quietly manipulated search engine rankings without affecting regular visitors. They also leveraged public privilege-escalation exploits (EfsPotato, BadPotato), and tools like GoToHTTP, Zunput, and web shells to maintain persistent access across sectors such as healthcare, education, retail, insurance, transportation, and technology. ESET attributes GhostRedirector to a China-aligned threat actor, citing Chinese code strings, a Chinese-issued code-signing certificate, and use of the password “huang.”
Sources: ESET, Hacker News, We Live Security
Key Takeaways
– SEO Abuse via Malware: Hackers used SEO fraud (via Gamshen) to covertly manipulate Google search rankings—and benefit gambling websites—without impacting normal site visitors.
– Resilient and Multi-Pronged Attack Strategy: The campaign combined custom backdoors (Rungan), privilege escalation exploits (EfsPotato, BadPotato), and other tools to embed long-term access across various global sectors.
– China-Linked Attribution: ESET links the campaign to China-aligned actors based on code traits, certificate origin, and internal details, though emphasis is on “China-aligned,” not definitive attribution.
In-Depth
Since late 2024, cybersecurity researchers have tracked a cunning new threat group known as GhostRedirector—a China-aligned, opportunistic operation that quietly infiltrated at least 65 Windows servers worldwide. Far from your typical ransomware gang, GhostRedirector specialized in “SEO fraud as a service”, executing a scheme that quietly manipulated Google’s search crawler (Googlebot) to boost gambling websites in search results.
The campaign relied on two custom malware tools: Rungan, a passive C++ backdoor capable of executing commands and creating admin users, and Gamshen, an IIS module that intercepted Googlebot requests to insert hidden backlinks or manipulated content aimed at deceiving search algorithms—without affecting normal visitors. Together, these tools allowed the hackers to quietly juice search rankings without arousing suspicion.
To gain and maintain access, the attackers exploited probable SQL injection vulnerabilities using PowerShell-driven payloads from a staging server (868id[.]com), along with public tools like EfsPotato and BadPotato for privilege escalation. They also deployed web shells, GoToHTTP, and custom utilities such as Zunput—all pointing to deliberate, layered persistence even if some components were removed.
Victims ranged across industries—from healthcare and education to retail and transportation—and spanned numerous countries, with strong representation in Latin America and Southeast Asia. That broad reach speaks to the opportunistic nature of this campaign, driven more by opportunity than by specific targets.
ESET attributes GhostRedirector to a China-aligned group based on linguistic cues, a code-signing certificate issued to a Chinese firm, and internal artifacts like the password “huang.” Still, attribution remains cautious, reflective of prudent cybersecurity norms.
In short, GhostRedirector underscores a subtle but insidious evolution in cyber threats—where search engine manipulation becomes the payload and stealth is the weapon.